In the context of BGP, a valley-free violation is when routing policy governing BGP path selection and advertisement breaks the valley-free policy. The valley-free routing policy basically ensures traffic doesn’t traverse unintended autonomous systems, usually a customer AS downstream from a service provider, and therefore an unintentional transit network.
The extended metaphor of hills and valleys is used to describe how end customers with their own AS will advertise their prefixes “upstream” or “uphill” to their local service provider. These providers will then advertise those prefixes to their BGP peers and uphill to Tier-1 service providers.
So, upstream or uphill is a way to visualize the direction of traffic in a hierarchical nature of customers and various levels of service providers.
So where does a valley come into play, and why is that bad? The idea is that a route should always go “downhill” from providers to customers or stay at the same level in peering relationships and should never go “uphill” from customers to providers without a corresponding downhill path.
In other words, an end customer’s traffic should go to a provider and then be forwarded only to peer providers or uphill providers to reach its destination, never back down to another customer acting as a transit network.
Take a look at the image below, and notice how the direction of traffic goes originating from Customer A in AS 1 and destined for Customer B in AS 2 goes up from Customer A to their local service provider and continues back down to its destination, another customer, in our example Customer B. This is the kind of behavior we want.
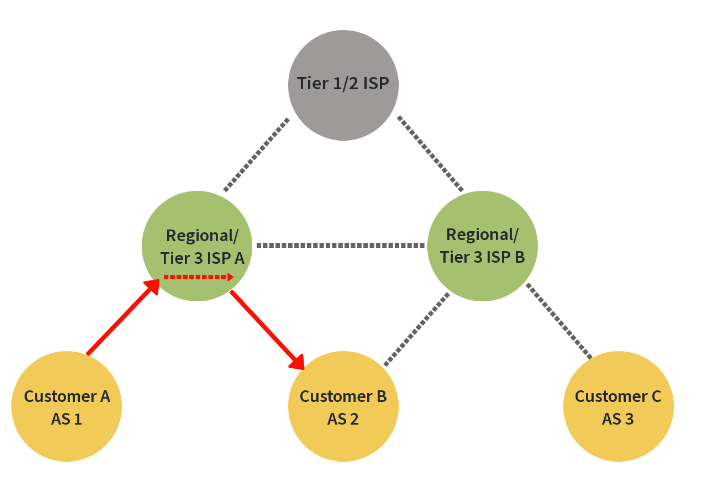
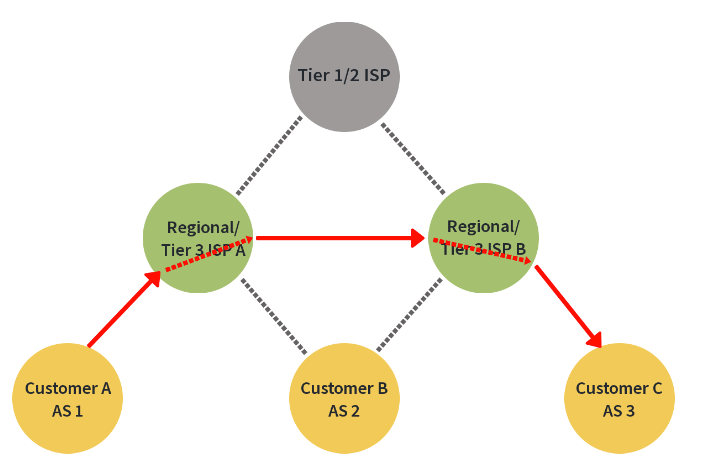
There are no valleys, no inefficient AS routing paths. Take a look at the next image, though, and notice that though traffic is bring routed from one ISP to another, in this case peer ISPs, there are still no problems violating the valley-free policy. Customer A is sending traffic to Customer C which traverses the regional ISPs laterally and then down to the destination.
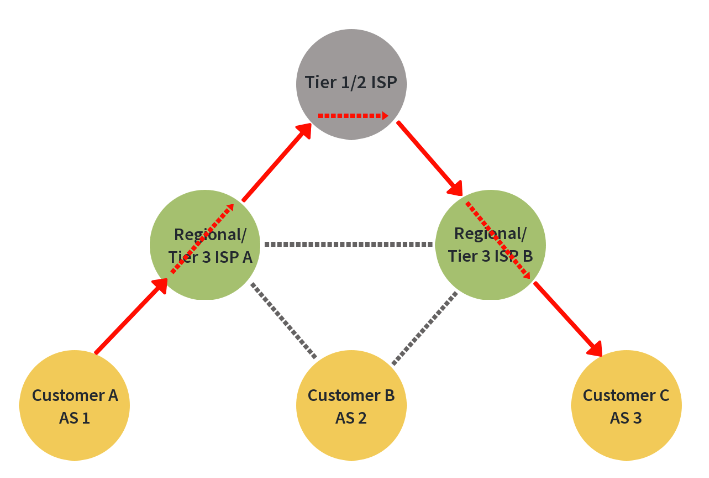
In the image below, we have traffic being forwarded from ISP A representing a Tier 3 or regional ISP uphill to a Tier 1 or Tier 2, or in other words a transit or possibly backbone provider. A valley-free violation occurs when a route does not adhere to this behavior and policy, so again, no problems here.
So let’s look at a valley-free violation, which remember, occurs when a route is sent back downhill to an unintended AS behaving as a transit network.
Take a look at the next image. Traffic from Customer A in As 1 is destined for Customer C in AS3 and is sent uphill to ISP A. However, ISP A doesn’t forward traffic laterally to ISP B or uphill to the Tier 1 ISP. Instead, it sends it back down to a network that isn’t it’s final destination, Customer B. Customer B, presumably being a dual-homed network, knows about Customer C via ISP B, so forwards the traffic back up to ISP B and then to its final destination thereby creating a valley route and violating the valley-free principle.
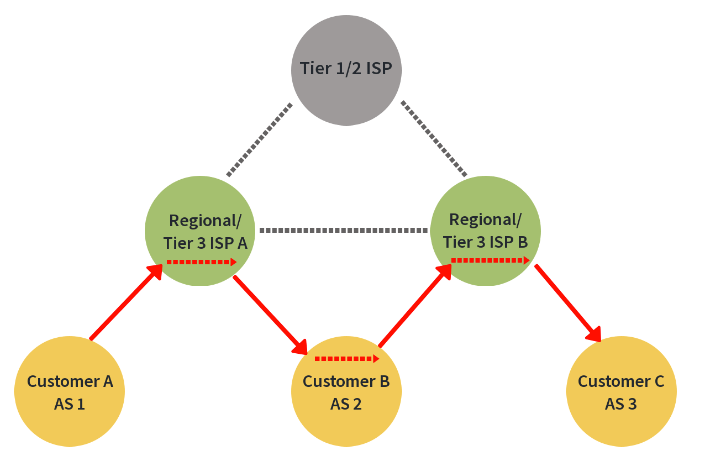
This is almost always unintended. ASes generally don’t want to transit traffic from one provider or peer to another without compensation, and that’s especially true of an end-customer that has no intention of being a transit network. In the image above, if Customer B is unintentionally acting as a transit network, usually a result of route leaks, they’re using their own hardware and software resources to route internet traffic, possibly large amounts of traffic, for free.
This behavior can also lead to inefficient routing on the internet which can increase latency and introduce potential security issues. An end-customer unintentionally acting as a transit network will probably not have the mechanisms in place, whether that be hardware, software, configuration, and so on, to route internet traffic with the same speed, efficiency, and security guarantees that a service provider would.
In practice, ASes implement BGP route filtering to enforce valley-free routing and avoid this scenario. However, due to the complex and decentralized nature of the internet, violations can still occur, usually unintentionally such as misconfigurations or missing filters.
Thanks,
Phil

Leave a comment