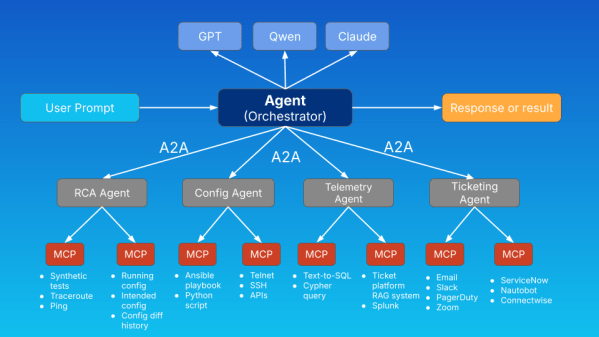
Over the last year, we’ve seen explosive interest in agentic AI systems built with LLM-powered components that can reason, plan, call tools, and coordinate with other agents. But if you’ve actually tried to build a multi-agent workflow, whether for network automation, observability, or network incident response, you’ve probably run into one glaring problem – all agents don’t speak the same language.
Continue reading “Understanding the A2A Protocol for Agentic AI in Network Operations”A Network Engineer’s Guide to Understanding the Model Context Protocol for AI Integration
If you work in technology long enough, every new framework starts to sound like “yet another API layer.” The Model Context Protocol (MCP) is different. It’s not a product, and it’s not tied to any one vendor or model. It’s an open standard for how AI apps talk to tools and data providing a standardized, model-agnostic way for AI apps to access external tools and data.
Continue reading “A Network Engineer’s Guide to Understanding the Model Context Protocol for AI Integration”Is Cisco’s Unified Edge A Step Toward Agentic AI at the Edge or Just Clever Packaging?
Cisco’s latest announcement at Partner Summit 2025 introduced Cisco Unified Edge, a converged compute platform designed to bring agentic and inferencing AI workloads closer to where data is actually generated, such as the branch, the factory, the retail floor, or the hospital wing. The idea is that instead of sending massive data streams back and forth to the data center or cloud, we can perform inference and decision-making locally for faster responses, lower bandwidth requirements, and higher resilience.
It’s an interesting, ambitious, and I think logical idea that extends Cisco’s networking footprint into edge computing and AI infrastructure, which are arguably two of the fastest-moving segments in enterprise IT.
Continue reading “Is Cisco’s Unified Edge A Step Toward Agentic AI at the Edge or Just Clever Packaging?”The Goal of AI in ITOps is Operational Improvement
I’ve been speaking with more folks again recently about AI initiatives in their IT organizations. Most recently it was a systems team that ran the on-prem server infrastructure, Azure environment, and just recently also tasked with end-user computing.
What struck me in the conversation was how the discussion kept going back to AI. That might seem weird for me to say considering the goal was to discuss AI initiatives, but let me explain.
AI is a technology; it’s a tool. Yes, I understand that in reality AI is a complex and sophisticated family of technologies, but ultimately it’s still a tool. So unless you’re literally building models and live in academia or the world of R&D, AI is not a goal unto itself. Starting with AI was the wrong approach in the discussion with this systems team, and it’s usually the wrong approach for any team.
For most of us in our respective niche of IT operations, the goal of AI is operational improvement.
Continue reading “The Goal of AI in ITOps is Operational Improvement”Three Critical Questions Before You Consider AI in NetOps
A few months ago I read Kavita Ganesan’s excellent book, The Business Case for AI: A Leader’s Guide to AI Strategies, Best Practices & Real-World Applications. I highly recommend it to anyone thinking critically about implementing an AI solution in IT operations because the concepts and best practices she outlines helped me to think more practically about implementing AI solutions in IT operations.
Continue reading “Three Critical Questions Before You Consider AI in NetOps”AI in NetOps is not about replacement – it’s about evolution
A good friend of mine is an electrical engineer for a well-known passenger train company in the United States, and we recently talked about how his job, his entire career, has taken a turn from traditional electrical engineering to computer systems integrations and building telemetry pipelines. In other words, as the industry progressed, he wasn’t replaced. Instead, his role evolved.
That probably isn’t a groundbreaking revelation considering almost every industry has been impacted by some form of digitization. Things change, and people adapt. However, what really intrigued me was the new initiative to use AI to augment the train management system.
Continue reading “AI in NetOps is not about replacement – it’s about evolution”Using an LLM to Query Structured Network Telemetry
One practical use-case for using large language models in network operations is to help query large datasets of network telemetry faster and more easily by using natural language. This can improve NetOps and facilitate better data-driven insights for engineers and business leaders. However, the volume and nature of the data types we commonly utilize in networking makes this a daunting workflow to build, hence the dichotomy of build vs. buy.
There are network vendors building natural language query tools for network telemetry, and so it’s important to understand the value, components, and fundamental workflow whether you’re researching vendors or building your own proof of concept.
A reasonable approach, even just to experiment, is to start very simple, such as querying only one data type. That way, we can ensure accuracy and see meaningful results right away. In time, we can build on this initial workflow to include more types of data, perform more advanced analytics, and automate tasks.
Continue reading “Using an LLM to Query Structured Network Telemetry”Beginner’s Guide for Using Large Language Models in Network Operations
Large language models like GPT, Claude, Llama, and others have the potential to transform network operations. We’re familiar with how they help us generate code, summarize texts, and answer basic questions, but until recently their application to network operations has been suspect. However, it was just a matter of time until we understood the use-cases and how to mitigate some of the initial problems like hallucinations and data privacy.
I believe there are two main use-cases right now, with a third right around the corner. First, LLMs can query large and diverse datasets of network telemetry faster than any engineer, which in turn reduces resolution time and increases network performance and reliability. Second, as part of a larger workflow, LLMs can help us perform advanced analysis on network telemetry thereby providing greater insight and understanding of what is otherwise a complex web of varied telemetry data. And in the near future, agentic AI, which is really an extension of my second use case, will help us automate tasks and more autonomously manage network operations.
In this post we’ll discuss the first two use-cases and touch on the third. We’ll also unpack some of the limitations we face implementing LLMs in NetOps, and we’ll discuss several quick and easy ways to get started right now.
Continue reading “Beginner’s Guide for Using Large Language Models in Network Operations”Packets
Hey networking community!
To get you through another week of cutovers, pcaps, and folks blaming the network when it’s yet another DNS issue, I made this song parody just for you 🙂
It’s called Packets, based on one of the best songs to hit the airwaves in February 1996, and in my humblest of opinions, it’s the perfect soundtrack for your next 2am change window…
Enjoy!
(the lyrics are in the post for your viewing convenience)
10 Books Every Network Engineer Should Read
These are 10 books that have been foundational for me personally in my career as a network engineer. I left out the Cisco CCNA, CCNP, and CCIE textbooks, though they were all mostly fantastic. However, this list below has been great for me as foundational networking knowledge in a well-written format.
Toward the bottom are several books that I’ve read much more recently, including books about network automation and machine learning in networking. Personally, for anyone seeking to get into network engineering or to become a more well-rounded networking professional, I recommend topics around automation and ML as well.
Continue reading “10 Books Every Network Engineer Should Read”From Manhattan to the Mohawk with the Upstate (NY)NUG
You can split New York State into several regions, though the exact areas are often hotly debated depending on if you say soda, pop, or know all too well what time the last train leaves Penn Station. When Zig Zsiga and I started the New York Networking Users Group, the idea was to continue with the existing (NY)NUG which had one successful event in Manhattan. But after thinking about it, I thought it would be great to start multiple chapters around the state to accommodate all those crazy different accents (seriously – every region in New York State has a different accent and I love it).
And thus began a brand new chapter of the (US)NUA: the Upstate (NY)NUG.
Continue reading “From Manhattan to the Mohawk with the Upstate (NY)NUG”Best Practices for Enhancing BGP Security
BGP is the de facto routing protocol for inter-domain routing, or in other words, the global internet. It’s used to exchange routing information among autonomous systems around the entire world. Therefore, it’s extremely important we do what we can to secure BGP communications, what we advertise, and the methods we use to create peering relationships. However, BGP is decentralized in nature and generally built on trust between BGP peers making it difficult to secure and a popular attack vector.
For this post, I’ll focus on two main threats to BGP security and several (but not all) methods we can use to mitigate BGP security incidents.
Continue reading “Best Practices for Enhancing BGP Security”What is a valley-free violation?
In the context of BGP, a valley-free violation is when routing policy governing BGP path selection and advertisement breaks the valley-free policy. The valley-free routing policy basically ensures traffic doesn’t traverse unintended autonomous systems, usually a customer AS downstream from a service provider, and therefore an unintentional transit network.
Continue reading “What is a valley-free violation?”The (US)NUA – A New Networking Community
I love the networking community, and I attribute much of my success as a network engineer, network architect, and now a technical marketer, to the interactions I’ve had with other network pros over the years. That’s meant interaction on Twitter, Reddit, the big conferences, and the small events like Tech Field Day. From those sprang up private Slack and Discord groups, the occasional iMessage or Google Hangouts group, and so on.
That changed significantly during the pandemic. Both the large and small conferences, meetups, and even company events stopped altogether and didn’t come back for a few years. And when they did, they were different. I noticed the large events weren’t as large (although I’m always shocked by how many people are at re:Invent), and the hybrid conference idea didn’t work for me. I missed the days of attending sessions, chatting with people over coffee in between keynotes, grabbing drinks in the evening with old nerd-friends, and getting to interact in person, engineer-to-engineer.
We needed a new networking community.
Continue reading “The (US)NUA – A New Networking Community”A Breakdown of MELT for Observability
Here’s a short breakdown of MELT, which stands for metrics, events, logs, and traces. These are the four most basic data types used for network and system telemetry. There are other data types that are widely used and very useful in a robust observability solution, though I would argue some are just another form of one of these general data types.
These data types are used in system monitoring in general, but are very valuable in observability. Metrics, events, logs, and traces have most commonly been the cornerstone of application and system observability, but today they also form key components of the telelemtry used for network observability.
Continue reading “A Breakdown of MELT for Observability”10 Networking Tools to Keep in Your Bag
I was a VAR network engineer for years. I worked on location in data centers and network closets to install network gear, perform various types of cutovers, and troubleshoot network problems. Even when I moved to a solutions architect role, I always kept several items with me at all times in my laptop bag when going on-site, just in case. Some items are obvious, and some I carried because I got burned when I didn’t have it with me that one time.
If you’re a network engineer managing your own network or your customers’ network, here’s a list of 10 networking tools that you should consider keeping in your bag.
Continue reading “10 Networking Tools to Keep in Your Bag”Top 7 Network Engineering Conferences Ranked
Here’s a list of my favorite networking-focused events ranked with number 1 being the best. “Best” means a conference or event that either had a ton of relevant networking content for me personally or that helped me directly in my career (for example, I’ve never been focused on storage at all – therefore you won’t see those events that on my list).
So if you’re in the networking field like me, check out these events and feel free to disagree in the comments or on the socials 🙂
Continue reading “Top 7 Network Engineering Conferences Ranked”Five Ways to Jump Start Your Career in Tech in 2021
I’ve been in tech long enough to know what’s worked for me as far as growing my career as a network engineer. So looking at the networking industry today in early 2021 and looking back at what’s worked for me, I’d like to share five things I believe can help you take your career in tech to the next level.
Continue reading “Five Ways to Jump Start Your Career in Tech in 2021”Where is Intent Based Networking in 2021?
Intent Based Networking certainly became a popular term over the last couple years. I don’t hear about it much anymore in terms of new and upcoming tech, though. I hear the term being used almost as a side comment when vendors say things like, “oh yeah we do intent based networking – it’s built right into our GUI.”
So after all the marketing hype, the buzzword bingo, and as much digital transformation as we can stomach, where are we with intent based networking in 2021?
Continue reading “Where is Intent Based Networking in 2021?”