I spent about a year completely focused on network security, and one thing I learned was that spending all my time focused on securing the perimeter to the neglect of intra-LAN traffic was a recipe for disaster.
Most of the traffic in our data centers is east-west, with only a small fraction actually being northbound out to the rest of the world. The cost of massive firewall appliance clusters operating at line-rate is astronomical, and it doesn’t make sense to punt traffic all over the place if there’s a better way.
For years we’ve written ACLs on core switches and deployed massive data center firewalls to segment our servers, but VMware has been taking security much closer to the endpoints themselves with their brand of distributed firewall. Last January at Networking Field Day 17, Geoff Wilmington, Senior Technical Product Manager, NSBU, took us on a deep dive presentation into the nuts and bolts of VMware’s context-aware micro-segmentation solution.
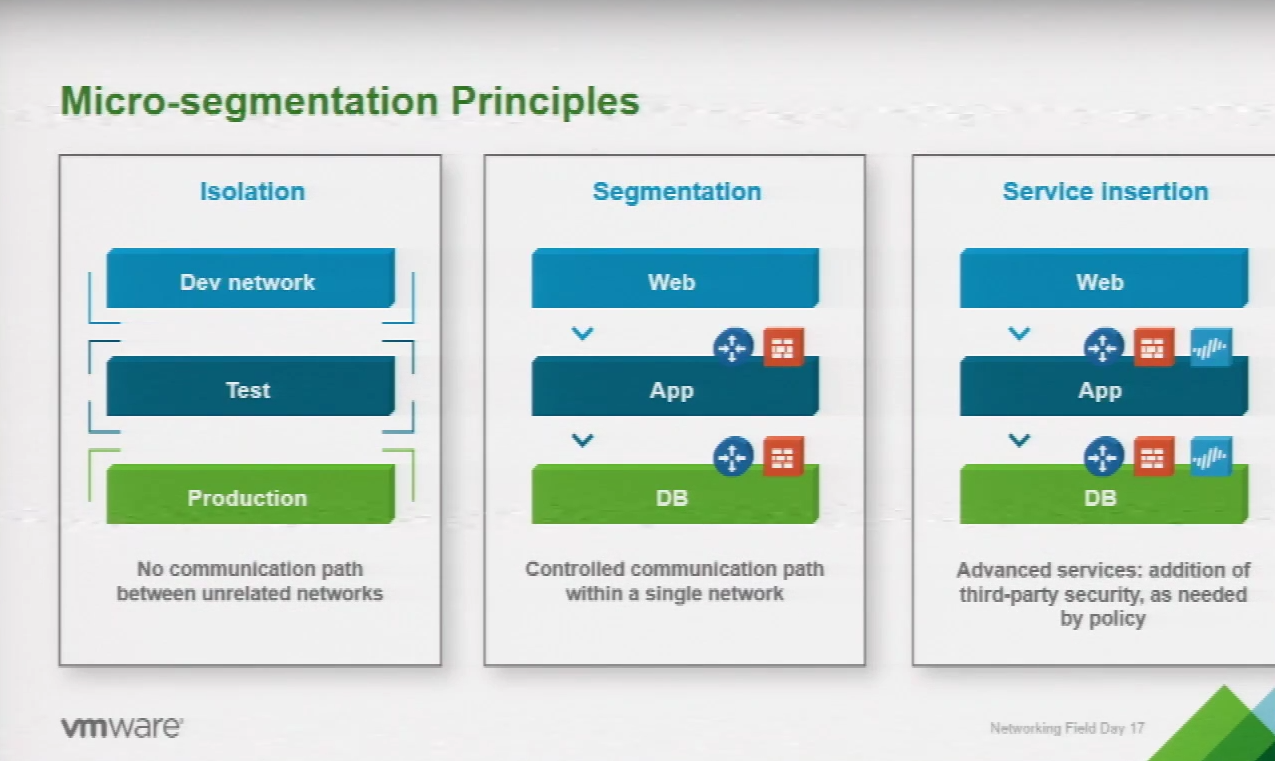
Micro-segmentation is about isolation among parts of your network even if the devices exist in the same IP address space. VMware’s micro-segmentation strategy is to segment the actual tiers of an application, such as the front end, database, etc, in order to provide stateful firewall services at the virtual machine level itself. For example, a network admin would not only be able to lock down a VM to one network port such as HTTPS but actually lock down an application or database tier from another further decreasing its attack surface.

Built right into VMware NSX, this distributed context-based firewall collects flow data from vNICs on VMs and feeds it into flow tables forming the basis of the distributed firewall rules. This is important because it means each VM has its own firewall perimeter solving the problem of having to shift traffic around the data center to inspect it.
VMware NSX is simplifying network security by bringing security right down to the application itself.
The distributed firewall module is in the actual kernel of every hypervisor allowing firewall services to easily scale horizontally. Each individual VM running its own firewall at first glance might seem more complex, not less, but because firewall policies are created for logical groups rather than at the network edge, configuring the distributed firewall is actually more simple.

All firewall rules are managed centrally as logical groups in NSX. Because NSX integrates fully with vCenter, a network administrator can configure rules for applications based on workflows rather than IP addresses and MAC addresses. And since rules are applied to workflows at the application tier, rules actually follow VMs as they move from host to host.
Putting the firewall at the kernel level means that firewall throughput is near line-rate – a very expensive proposition in hardware-based traditional data center firewalls. And in case you were worried running a firewall this way would chew up all your CPU cycles, the good news is that typically you’ll see consumption of about only 3% – 5% CPU utilization related to firewall services.
VMware’s context-aware micro-segmentation capabilities are largely based on a 5-tuple identification with growing capabilities for more identification factors. Geoff explained that the 5-tuple method is still the primary way to create firewall policy, and this was a little disappointing to hear. The 5-tuple method looks at 5 aspects of network traffic including the source and destination IP address as well as port numbers and protocol.
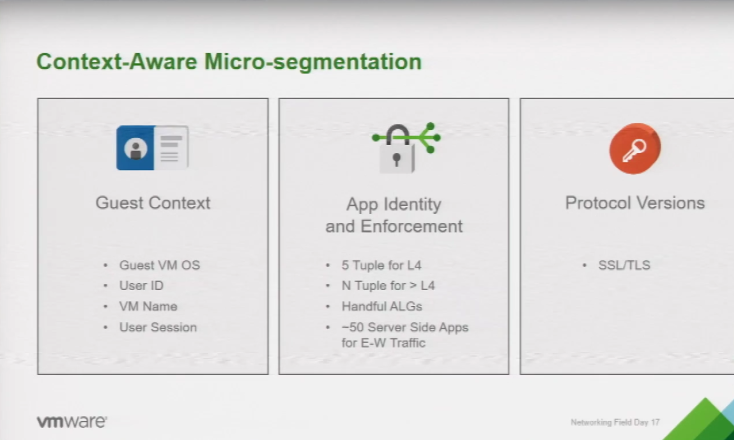
At the time of VMware’s presentation they did support about 50 server side applications for east-west traffic, which, I hope, will increase significantly. That’s at the heart of the problem VMware is trying to solve, namely, the complexity of effectively securing east-west workflow traffic.
Geoff concluded by stating very frankly that micro-segmentation isn’t easy – it’s a process. VMware’s goal is to take the complexity out of micro-segmentation so engineers can benefit from the increased security posture without having to also increase their workload.
The Application Rule Manager was introduced in NSX 6.3 as the toolset to automate this process and simplify identifying workflows and creating rules. With ARM we can take advantage of the distributed firewall platform without having to figure out and manage innumerable rules.

I really like the concept of pushing security closer and closer to the endpoint and focusing on application flows rather than only network parameters. It provides more granular firewall control and a better security posture. The only issue is the daunting task of managing hundreds if not thousands of potential firewalls individually. VMware solves this problem with their context-aware distributed firewall built in to NSX and with the automation of the Application Rule Manager.
My short time focused on network security was mostly about wondering how I could secure traffic without an entire team of engineers. VMware’s developing approach gives us the ability to micro-segment our data centers in one single platform.
Disclaimer: Gelstalt IT, the organizers of Networking Field Day, provides travel and expenses for me to attend Networking Field Day. I do not receive cash compensation as a delegate. Also, I do not receive compensation for writing about or promoting Networking Field Day.

Security is so important and a topic that I frequently need to discuss with my clients. Although we provide them with safe and secure systems, there are still many errors they can make by themselves
LikeLike